In his Hoover Institution Essay, A Rubicon, Dan Geer, the Chief Information Security Officer of In-Q-Tel and an epidemiologist by training, brings to the forefront the central issue of all security:
“We call that on which we most depend “critical infrastructure.” Because dependence is transitive, so is risk. That you may not yourself depend on something directly does not mean that you do not depend on it indirectly. We call the transitive reach of dependence “interdependence,” which is to say, correlated risk. Interdependence within society today is centered on the Internet beyond all other dependencies… Our concern is unacknowledged correlated risk.”
Interconnected, unacknowledged risk is where failures, data breaches, and loss of data quality occurs. But further complicating the issue, our beneficiaries are rarely in a position to even know what it is they depend on, or worry about their right to privacy. It is just too far removed from the day to day concerns of an individual worried about food security or access to healthcare. What this means, is that we are under an ethical obligation to protect the privacy and information of our beneficiaries.
What do you depend on?
I contend that this is the fundamental question of information security for INGOs and non-profits. In order to be able to accurately answer the question, an organization needs to be able to succinctly articulate:
- What data is being collected?
- Who owns the data?
- What is the data used for?
- Who has access to the data?
- What assets (computers, servers, phones) are being used?
- What technologies are being used?
- Who owns the processes themselves?
This is a daunting list, and chances are the answers to a lot of these questions are either unknown, or there isn’t an individual with an ownership claim to the process or the data. That’s okay.
What we’ve found at Dharma Platform, from dozens of engagements with ministries of health, non-profits, and INGOs, is that no one has the answers to all of these questions. In fact, in my work at Kenna Security with Fortune 1000 corporations, the same holds true. This is because security is not an end state; it is a continuous process of improvement. Security begins with making sure the questions above are being thought about actively. A good place to start is to ask them collectively as a group at the next board meeting.
As a result of applications moving closer to devices and users, and data becoming increasingly more challenging to analyze, organizations need to leverage cloud and mobile technologies with access to real-time data flows and analytics to remain effective.
Disparate solutions are one of the greatest security threats to social sector organizations. Every step of the process presents a risk for data loss or exposure. Faced with limited capacity and resources, many nonprofits turn to free solutions like Excel, Google Forms, MailChimp, and Survey Monkey. These free solutions added to the other steps of data flow — staff, computers, phones, etc. — means security can present a real problem.
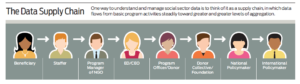
Here are some steps to start reducing risk:
- Build a culture of awareness, ownership, and responsibility around organizational and beneficiary data.
- Clean up the process and limit the number of steps.
- Document the revised process and train your team on how to reduce the risks.
This presents a particular security paradox for nonprofits, NGOs, and other local actors: while technology offerings and capacities are increasingly more plentiful and robust, the best way to ensure a secure data flow is to reduce complexity.
Michael Rotyman contributed this article for the 2019 ICT4D Conference in Kampala, Uganda this April.

Michael Roytman
With a background focusing on cybersecurity data science and Bayesian algorithms, Michael has worked with Doctors Without Borders, The World Health Organization, and the UN as a technical advisor. After co-founding Dharma Platform, Michael landed on the 2017 Forbes 30 under 30 list. He is the Chief Data Scientist at Kenna Security and holds an M.S. in Operations Research from Georgia Tech.







